- Universal changes across the all areas of the CAPEC schema.
- String fields that were meant to capture complex textual data have been converted from simple strings to a new Structured_Text_Type that will enable structured text data including titles, paragraphing, code snippets, and image references.
- All elements that can have multiple entries are now encapsulated in plural container elements for consistency.
- The schema root element has been changed from Common_Attack_Pattern_Enumeration to a more encompassing Attack_Pattern_Catalog with attributes to capture Name, Version and Date. This will help us to better manage the ongoing growth and maturation of CAPEC.
- Two completely new concepts were added to the schema to support enhanced description of the attack patterns targeted at additional use cases for the CAPEC content: Attack_Surfaces and Observables.
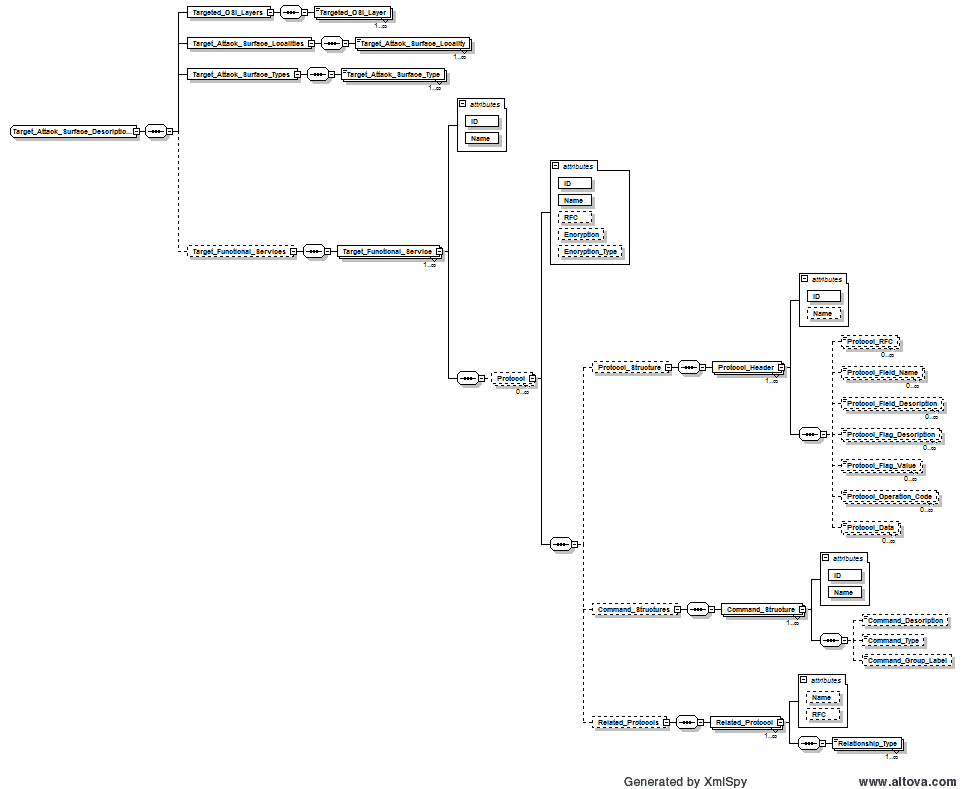
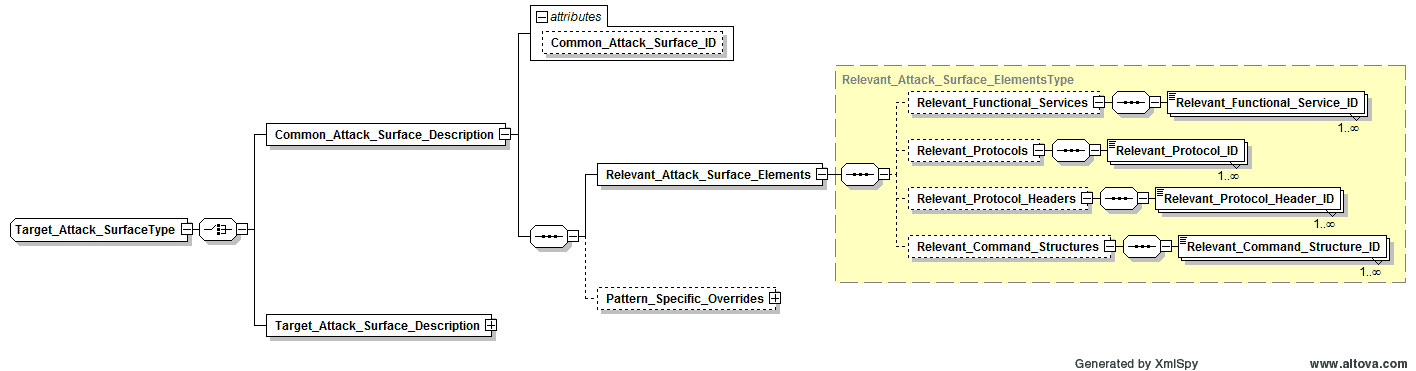
- Attack_Surfaces – The Target_Attack_Surface element was added as an introductory attempt to capture and communicate the nature of the target attack surface that a given attack pattern focuses on. This can enable better granularity within patterns by allowing different pattern sub-elements to reference the areas of the attack surface that are relevant to them. It can also enable better modularity and reuse of attack patterns during architectural risk analysis. It is very well understood that this first cut at an attack surface structure is limited and in need of expansion/enhancement. It is expected that this structure will gain more breadth and refinement over time. This first cut is aimed primarily at supporting the addition of network attack patterns to the CAPEC content.
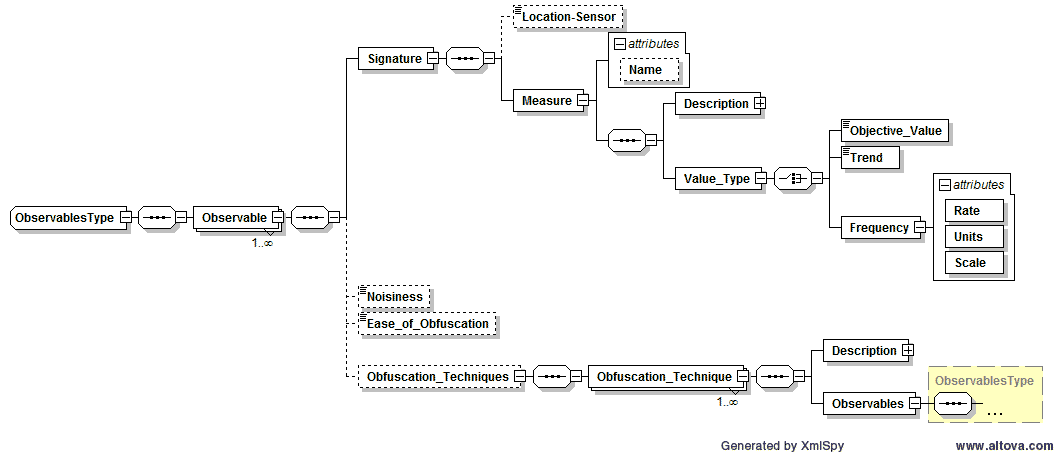
- Observables – The Observable element was added as a first step toward integrating CAPEC's top-down view of patterns of attack with the bottom-up view of the security operations and incident response community. The objective is to enable tagging of certain CAPEC sub-elements (e.g., Attack_Step, Attack_Step_Technique, Outcome, Security_Control) with objective data signatures that would be observable through various operational sensors when that event occurs or that property is present. The integration of these two domains along their common axis of focus ("Attack") has great potential to benefit both communities.
- Several new high-level object types were added to the CAPEC catalog in addition to Attack_Patterns.
- Views – The View object has been created to allow the capture and presentation of multiple different perspectives on the CAPEC content and its inter-relationships. These View objects are very similar to those in the Common Weakness Enumeration (CWE™).
- Categories – The Category object has been created to act as a collection of attack patterns sharing a common attribute, such as CAPEC-172 Time and State Attacks or CAPEC-212 Functionality Misuse. These Category objects are very similar to those in CWE.
- Compound Elements – The Compound_Element object has been created to capture and reference patterns of attack that are known by a given name in the industry but, in actuality, consist of a combination of multiple attack patterns executed in a sequential or non-sequential manner. Sequentially executed attack patterns are captured as Chains while non-sequentially executed patterns are captured as Composites. The Compound_Element object and it Chains and Composites flavors are very similar to the Compound_Element object in CWE.
- Two new global abstraction object types were added to the CAPEC catalog to enable more effective and efficient reuse of common content across patterns: Common_Attack_Steps and Common_Attack_Surfaces.
- Common Attack Steps were added to capture the content of attack steps that are shared in their basic form across numerous attack patterns. By abstracting them out, we can simplify the management of that content in one location as well as reduce redundancy and the overall size of the CAPEC content files.
- Common Attack Surfaces were added to abstract out and capture specific common attack surfaces that are likely to be targeted by multiple attack patterns. Like Common Attack Steps, by abstracting them out, we can simplify the management of that content in one location as well as reduce redundancy and the overall size of the CAPEC content files.
- A wide range of improvements and additions were made to the Attack_Patterns portions of the CAPEC schema. These changes include:
- New Pattern_Completeness attribute value (Hook) to capture named attack patterns that do not yet have basic description information to make them stubs. All top-level Attack_Pattern sub-elements are now optional to support pattern Hooks.
- New Status attribute (values = Deprecated, Incomplete, Draft, Usable, or Stable) to communicate the level of maturity that the creation/authoring of a particular pattern or other high-level object is at.
- All major elements in Attack Execution Flows and Target_Attack_Surfaces now have IDs assigned (in a much simpler integer format than the previous alphanumeric ones). These consistent IDs yield the ability to reference various individual execution threads through a given attack pattern or to reference individual items along those threads. This is a key capability for improving the usefulness of CAPEC as a test case enumeration tool and as a capability reference in attack tool comparison and evaluation.
- Attack_Step was broken into a choice between Common_Attack_Step or Custom_Attack_Step to enable the efficiencies yielded by Common_Attack_Steps described above. Common_Attack_Step allows reference to the ID of a globally defined Common_Attack_Step and then provides pattern-specific overrides for the field values in the common attack step definition for specializing it for local flavor.
- Attack_Step now allows specifying Observables (described above) for that Attack_Step
- Attack_Step_Technique now allow referencing of leveraged attack patterns and relevant attack surface elements (can reference various elements of the attack surface defined within the pattern), as well as specifying Observables (described above) for that technique
- Indicator now allows referencing relevant attack surface elements.
- Outcome now allows referencing relevant attack surface elements as well as specifying Observables (described above) for that Outcome.
- Security_Control now allows referencing relevant attack surface elements as well as specifying Observables (described above) for that Security_Control.
- New element Alternate_Terms added to capture other names this attack pattern may be known as.
- Example-Instance now has a References sub-element to enable capturing of references for that Example-Instance.
- Attack_Skill_or_Knowledge_Required is now structured into two sub-elements, Skill_or_Knowledge_Level (Low, Medium or High) and Skill_or_Knowledge_Type (Structured_Text_Type) rather than one simple text string in order to enable more structured content manipulation.
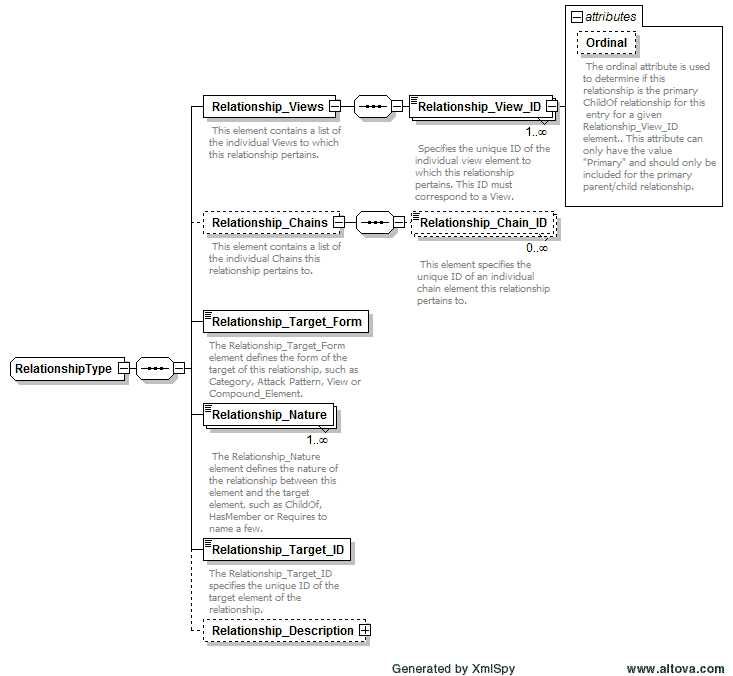
- Related_Attack_Pattern is now of the universal Relationship_Type (shared with Views, Categories and Compound_Elements) that captures CAPEC inter-object relationships in a consistent manner.
- The redundant Context_Description field has been removed and all content integrated into the Technical_Context element.
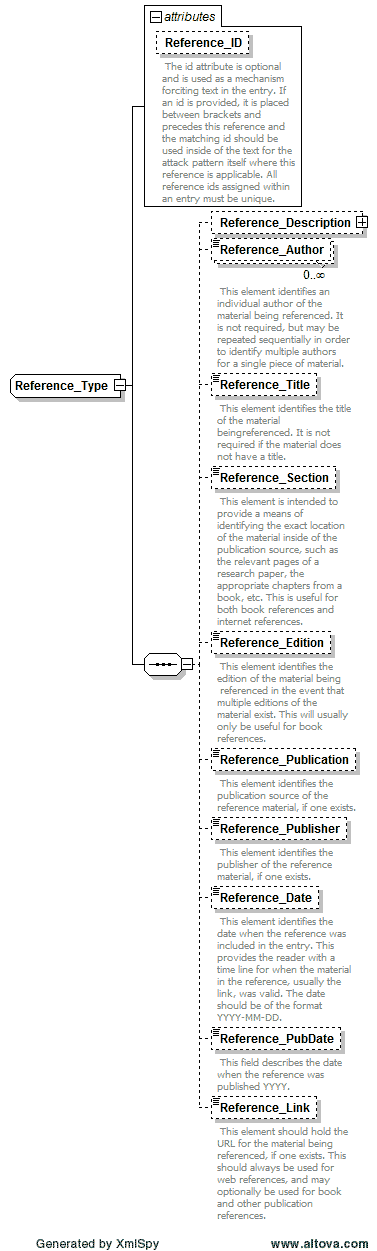
- The Reference element has been restructured into a much more comprehensive and descriptive structure.
- A new Other_Notes element was added to provide any additional notes or comments that cannot be captured using other elements. New elements might be defined in the future to contain this information.
- A new Maintenance_Notes element was added to contain significant maintenance tasks within this entry that still need to be addressed, such as clarifying the concepts involved or improving relationships. It should be filled out in any entry that is still undergoing significant review by the CAPEC Team.
- The Source element was converted into a much more comprehensive Content_History element to better track the change history of this entry.
News & Events2009 Archive
November 6, 2009
November 6, 2009 Making Security Measurable Briefing and Booth at ITSecurity Automation Conference 2009 MITRE presented a Making Security Measurable briefing and hosted a Making Security Measurable booth at the U.S. National Institute of Standards and Technology's (NIST) 5th Annual IT Security Automation Conference on October 26-29, 2009 in Baltimore, Maryland, USA. Visit the CAPEC Calendar for information on this and other events. CAPEC/CWE Briefing at CSI Annual Conference CAPEC/CWE Program Manager Robert A. Martin presented a briefing about CAPEC/Common Weakness Enumeration (CWE™) at the CSI Annual Conference on October 26-29 , 2009 in Washington, D.C., USA. Visit the CAPEC Calendar for information on this and other events. CAPEC/CWE Briefing at George Mason University CAPEC/CWE Program Manager Robert A. Martin presented a briefing about CAPEC/Common Weakness Enumeration (CWE™) on October 27 , 2009 as a guest lecturer at an IT Security Course at George Mason University in Fairfax, Virginia , USA. Visit the CAPEC Calendar for information on this and other events. CAPEC/CWE Briefing at SC World Congress CAPEC/CWE Program Manager Robert A. Martin presented a briefing about CAPEC/Common Weakness Enumeration (CWE™) at the SC World Congress on October 13-14, 2009 in New York, New York , USA. Visit the CAPEC Calendar for information on this and other events.
October 1, 2009
October 1, 2009 CAPEC/Making Security Measurable Booth at IT Security Automation Conference 2009, October 26-29 MITRE is scheduled to host a Making Security Measurable booth at the U.S. National Institute of Standards and Technology's (NIST) 5th Annual IT Security Automation Conference on October 26-29, 2009 in Baltimore, Maryland, USA. Visit the CAPEC Calendar page for information on this and other upcoming events. CAPEC and CWE Are Topics of Discussion at 10th International Common Criteria Conference CAPEC/CWE Project Leader Robert Martin, and Miguel Bañón on behalf of the Spanish Common Criteria Certification Body, presented a two-part talk about CAPEC and CWE and how version 4 of Common Criteria could leverage the two standards efforts at the 10th International Common Criteria Conference in Tromso, Norway, on September 22-24, 2009. The content of the two talks reflected the preliminary results of some of the improvement processes that will lead to the next major version of the Common Criteria. The conference itself focused on the evolution and enhancement of Common Criteria and the community of organizations working with it. Visit the CAPEC Calendar page for information on this and other upcoming events. Making Security Measurable Main Topic of Article in CrossTalk, The Journal of Defense Engineering An article entitled "Making Security Measurable and Manageable" by CAPEC/CWE Program Manager Robert A. Martin was published in the September/October 2009 issue of CrossTalk, The Journal of Defense Engineering. The article explains how measurable security and automation can be achieved by having government and public efforts address the creation, adoption, operation, and sustainment of their information security infrastructures in a holistic manner and by using common, standardized concepts to define the data (CVE, CCE, CPE, CAPEC, CWE, etc.), communicating this information through standardized languages (OVAL, XCCDF, CEE, etc.), sharing the information in standardized ways (OVAL Repository, NVD, etc.), and adopting tools and services that adhere to these standards. CAPEC/CWE Briefings at 8th Annual QAI & QAAM Regional Conference CAPEC/CWE Co-Founder and Architect Sean Barnum presented a briefing about CAPEC/Common Weakness Enumeration (CWE™) at the 8th Annual QAI & QAAM Regional Conference on September 21-23, 2009 Baltimore, Maryland, USA. Visit the CAPEC Calendar page for information on this and other upcoming events. CAPEC/CWE Briefing at 2009 NSA NIAP CCEVS Validators Workshop CAPEC/CWE Program Manager Robert A. Martin presented a briefing about CAPEC/Common Weakness Enumeration (CWE™) at the 2009 NSA NIAP CCEVS Validators Workshop on September 10, 2009 in Linthicum, Maryland, USA. Visit the CAPEC Calendar page for information on this and other upcoming events.
September 22, 2009
September 22, 2009 CAPEC List Version 1.4 Now Available CAPEC Version 1.4 has been posted on the CAPEC List page. This new release includes massive updates to the CAPEC schema as well as significant additions, improvements, and refinements to existing CAPEC content. CAPEC SCHEMA Listing every individual small change to the schema would take far too long so the following outlines the major changes to the schema that are included in this version. CAPEC CONTENT The CAPEC content of this release has three major changes and one minor change. Major Changes:
Minor Changes:
Comments are welcome on the CAPEC Researcher email discussion list. Future updates will be noted here and on the CAPEC Researcher list.
September 15, 2009
September 15, 2009 CAPEC List Version 1.3.2 Now Available CAPEC Version 1.3.2 has been posted on the CAPEC List page. This new release includes a minor update to the attack_taxonomy. Comments are welcome on the CAPEC Researcher email discussion list. Future updates will be noted here and on the CAPEC Researcher list.
September 11, 2009
September 11, 2009 CAPEC/CWE Briefing at 2009 NSA NIAP CCEVS Validators Workshop, September 10 CAPEC/CWE Program Manager Robert A. Martin is scheduled to present a briefing about CAPEC/Common Weakness Enumeration (CWE™) at the 2009 NSA NIAP CCEVS Validators Workshop on September 10, 2009 in Linthicum, Maryland, USA. Visit the CAPEC Calendar page for information on this and other upcoming events. CAPEC/CWE Briefing at 10th International Common Criteria Conference, September 21-23 CAPEC/CWE Program Manager Robert A. Martin is scheduled to present a briefing about CAPEC/Common Weakness Enumeration (CWE™) at the 10th International Common Criteria Conference on September 21-23, 2009 in Tromso, Norway. Visit the CAPEC Calendar page for information on this and other upcoming events. CAPEC/CWE Briefings at 8th Annual QAI & QAAM Regional Conference, September 21-23 CAPEC/CWE Co-Founder and Architect Sean Barnum is scheduled to present a briefing about CAPEC/Common Weakness Enumeration (CWE™) at the 8th Annual QAI & QAAM Regional Conference on September 21-23, 2009 Baltimore, Maryland, USA. Visit the CAPEC Calendar page for information on this and other upcoming events. Making Security Measurable and CAPEC/CWE Briefings at GFIRST5: The 5 Pillars of Cyber Security CAPEC/CWE Program Manager Robert A. Martin presented a briefing about Making Security Measurable and Co-Founder and Architect Sean Barnum and Robert A. Martin a briefing about CAPEC/Common Weakness Enumeration (CWE™) at GFIRST5: The 5 Pillars of Cyber Security on August 24-28, 2009 in Atlanta, Georgia, USA. Visit the CAPEC Calendar page for information on this and other upcoming events.
August 26, 2009
August 26, 2009 MITRE Hosts 'Making Security Measurable' Booth at Black Hat Briefings 2009 CAPEC participated in a Making Security Measurable booth at Black Hat Briefings 2009 on July 29-30, 2009 at Caesars Palace Las Vegas in Las Vegas, Nevada, USA. Attendees learned how information security data standards facilitate both effective security process coordination and the use of automation to assess, manage, and improve the security posture of enterprise security information infrastructures. See photos below: 

Visit the CAPEC Calendar page for information on this and other upcoming events.
July 17, 2009
July 17, 2009 CAPEC List Version 1.3.1 Now Available CAPEC Version 1.3.1 has been posted on the CAPEC List page. This new release includes minor improvements and refinements to existing CAPEC content as well as a few additions, primary highlights of which include: clean-up of content accuracy, clarity and consistency across a limited set of the existing content; updated and refined mapping of attack patterns to relevant entries in the Common Weakness Enumeration (CWE™) specifically targeted at adding better mapping to the CWE/SANS Top 25 list; addition of 26 newly authored attack pattern stubs consisting of an assigned CAPEC-ID number and a minimal set of pattern content (Description, Attack_Prerequisites, Typical_Severity, Resources_Required) to enable identification and discrimination of each pattern that include 17 from the existing CAPEC Attack Taxonomy as well as 9 more dealing with Software Integrity Attacks; minor modification of both the CAPEC content schema (v1.8.1) and the CAPEC taxonomy schema (v1.1.1); and, clean-up, refinement and additions to the CAPEC Attack Taxonomy including some reorganization and the addition of a new top-level entry "Analytic Attacks." The new patterns for this version are listed below. New attack pattern stubs: CAPEC-184 - Software Integrity Attacks Comments are welcome on the CAPEC Researcher email discussion list. Future updates will be noted here and on the CAPEC Researcher list.
May 29, 2009
May 29, 2009 CAPEC List Version 1.3 Now Available CAPEC Version 1.3 has been posted on the CAPEC List page. This new version contains a great deal of improvement and refinement to existing CAPEC content as well as addition of a significant amount of new and useful content. Highlights for this version include: clean-up of content accuracy, clarity and consistency across a broad set of the existing content; updated and refined mapping of attack patterns to relevant entries in the Common Weakness Enumeration (CWE™); addition of 11 newly authored full attack patterns; update of 16 existing patterns with enhanced "attack flow" descriptions (bringing the total of such enhanced patterns to 41); addition of 71 newly authored attack pattern stubs (from the CAPEC Attack Taxonomy) consisting of an assigned CAPEC-ID number and a minimal set of pattern content (Description, Attack_Prerequisites, Typical_Severity, Resources_Required) to enable identification and discrimination of each pattern; minor modification of the CAPEC schema in the addition of a Pattern_Completeness attribute for each pattern to allow easy discrimination between attack pattern stubs and full attack patterns; and clean-up, refinement, and additions to the CAPEC Attack Taxonomy. The new and enhanced patterns for this version are listed below. Newly added full attack patterns: CAPEC-102 - Session Sidejacking Updated attack patterns with enhanced "attack flow" descriptions: CAPEC-6 - Argument Injection New attack pattern stubs: CAPEC-113 - API Abuse/Misuse Comments are welcome on the CAPEC Researcher email discussion list. Future updates will be noted here and on the CAPEC Researcher list.
May 31, 2007
May 31, 2007 CAPEC List Version 1 Now Available CAPEC Version 1 has been posted on the CAPEC List page. The initial content consists of 101 attack patterns covering a broad range of attack types and levels of abstraction as well as an initial draft of a classification taxonomy. This attack taxonomy is still very emergent and is intended to convey the relationships between types of attacks and to provide a potential targeting list for attack pattern creation. As such, this initial draft contains not only the 101 patterns already created, but also a broad range of other attack types that can be captured as attack patterns in the future. The classification taxonomy is available in the CAPEC List section of the CAPEC Web site as an expandable HTML tree with links to patterns that have been created. The patterns themselves are accessible through the taxonomy, via a full alphabetic listing, via a search by ID mechanism or individually using pages addressed by CAPEC-ID. Comments are welcome on the CAPEC Researcher email discussion list. Future updates will be noted here and on the CAPEC Researcher list.
March 17, 2007
March 17, 2007 MITRE Launches CAPEC Web Site MITRE has launched a new Web site to support the Common Attack Pattern Enumeration and Characterization (CAPEC) effort that like CWE is funded by the U.S. Department of Homeland Security as part of the Software Assurance Strategic Initiative of the National Cyber Security Division. Led by Cigital, Inc., CAPEC is a companion effort to CWE in that CAPEC is structuring and formalizing the discussion of the attack patterns that are used against the weaknesses described in CWE. The objective of CAPEC is to provide a publicly available catalog of attack patterns along with a comprehensive schema and classification taxonomy. During this initial review period the CAPEC Web site is hosting a draft schema and content that requires members of the software community to register in order to access the information and provide comments. In this way the catalog will continue to evolve safely with public participation and contributions to form a standard mechanism for identifying, collecting, refining, and sharing attack patterns among the software community. Please send any comments or concerns to capec@mitre.org. More information is available — Please select a different filter. |